|
|
[RoQ | Instantiations | Related work | Publications | Talks | People | Grants] |
|
|
|
[RoQ | Instantiations | Related work | Publications | Talks | People | Grants] |
|
RoQ attacks in a nutshell:What are RoQ attacks?Reduction of Quality (RoQ) attacks are a new breed of attacks that target adaptation mechanisms employed in current computing systems and networks. RoQ is pronounced as in "rock". How RoQ attacks target adaptation? RoQ attacks keep an adaptive mechanism oscillating between over-load and under-load conditions, all the time. How RoQ attacks are different from DoS attacks? Denial of Service (DoS) attacks rely on overwhelming the victim with load that constantly exceeds its capacity. RoQ attacks, on the other hand, optimize the attack traffic to produce the maximum damage, while keeping a low profile to avoid detection. RoQ attacks do not necessarily result in a complete denial of service. How RoQ attacks are different from Shrew attacks? Shrew attacks exploit the timeout mechanism of TCP resulting in a complete denial of service. RoQ attacks do not target this specific protocol setting, but they are a general class of dynamic exploits that target adaptation mechanisms wherever they are present (transport layer, application layer, mac layer, etc,...). Also, RoQ attacks aim to maximize the attack potency. What is an attack potency? The attack potency, "PI", is defined to be the ratio between the damage caused by an attack and the cost of mounting such an attack. A smart attacker would be interested in maximizing the damage per unit cost---i.e., maximizing the attack potency 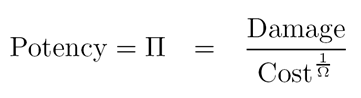 The above definition does not specify what constitutes "damage" and "cost". Throughout this work, we consider various instantiations of these metrics (e.g., bandwidth, delay jitter, etc..). Omega is introduced to model the aggressiveness of the attacker. A large Omega reflects the highest level of aggression, i.e., an attacker bent on inflicting the most damage and for whom cost is not a concern. Mounting a DoS attack is an example of such behavior. A small Omega reflects an attacker whose goal is to maximize damage with minimal exposure. What is the methodology used to assess the impact of RoQ attacks? We used a control-theoretic model to underline the complex interplay between the efficiency-load behavior of a resource and the adaptation mechanisms of both the resource and its consumers. The adaptation is modeled as an optimization process driving the system to a quiescent stable operating point. An optimized RoQ exploit would then keep the system oscillating between different states, in presence and absence of the attack traffic. We developed associated metrics to quantify the system's vulnerabilities. We present numerical and simulation results, which we validate with observations from real Internet experiments. What system designers need to do? System designers need to have the mind-set of cryptographers when modeling and building systems. Cryptographers, when designing their protocols, they model "Alice", "Bob" and "Eve". We, as system designers, tend to forget about "Eve"! Sure, we study our system under bursty traffic and sure we do stress testing to our systems. However, there is a big difference between the presence of bursty traffic and the presence of an adversary, who's main goal is to cause harm. |
This page is
currently maintained by
Mina Guirguis
Page last
updated April 2006